Data Security’s New Frontier: How Generative AI is Rewriting the Cybersecurity Playbook

Semantic Intelligence™ utilizes context-aware AI to discover structured and unstructured data across cloud and on-prem environments. The “Content Explorer” tab shows you the type of data you have (including category and subcategory), its location, and who has access to it.
The whispers in the cybersecurity hallways have grown into a roar. Generative AI isn’t just another technological trend – it’s a seismic shift that’s fundamentally transforming how organizations protect their most critical asset: data.
Karthik Krishnan, founder and CEO of Concentric AI, understands this landscape better than most. “Data is as foundational to an enterprise as identity or cloud or networking,” he explains, “and for something so foundational, data remains the most vulnerable threat surface.”
This vulnerability has never been more pronounced than in the age of generative AI.
Enterprises are now facing unprecedented challenges in maintaining data security, with employees potentially exposing sensitive information through public AI platforms like ChatGPT and Perplexity.
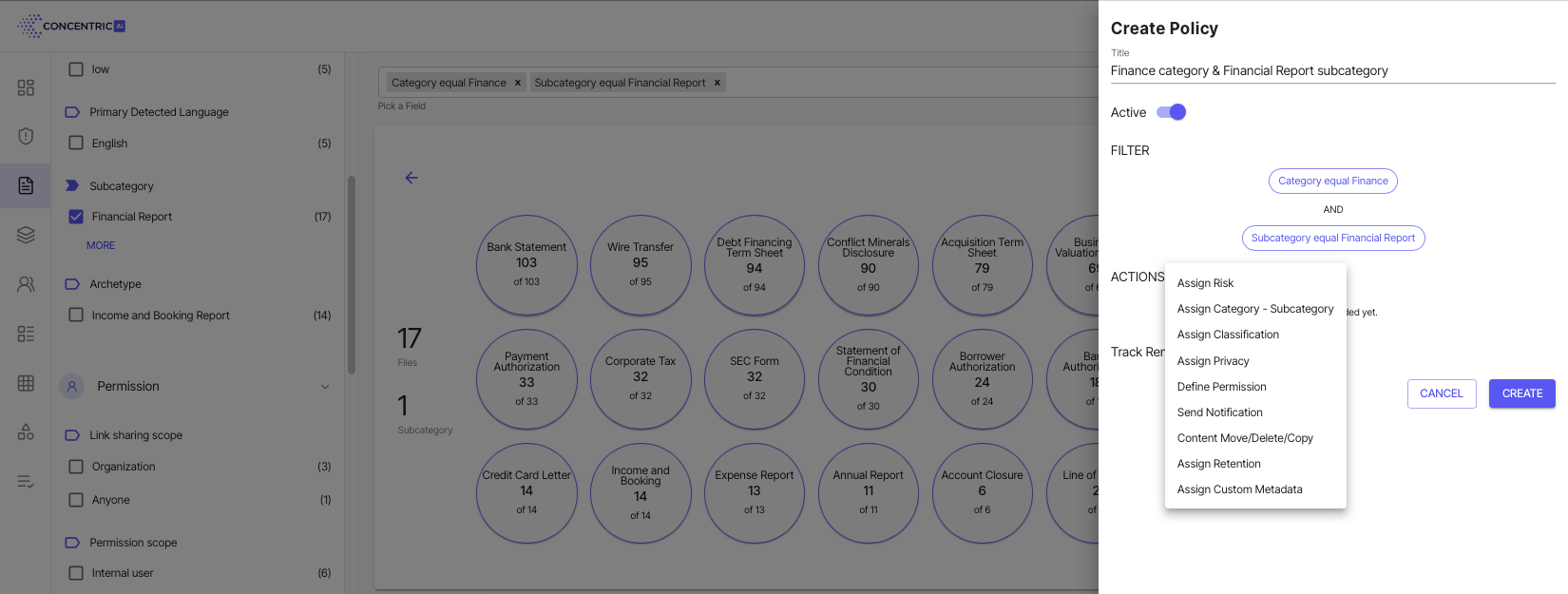
Users can filter data from the Semantic Intelligence “Content Explorer” and then select remediation actions using the “Create Policy” menu.
The Traditional Approach is Broken
For decades, organizations have relied on traditional data governance and data loss prevention (DLP) solutions that were fundamentally flawed.
These systems forced security teams to create complex policy matrices, regular expression patterns, and rule-based matching that generated more noise than insight.
“Most enterprise customers are still struggling to operationalize data security,” Krishnan notes. “Even after two decades of deploying data governance products, they still can’t answer basic questions like ‘Where is my sensitive data?’ Much less understand where that data might be at risk.”
The result? Security teams drowning in false positives, unable to distinguish between genuine threats and benign data interactions.
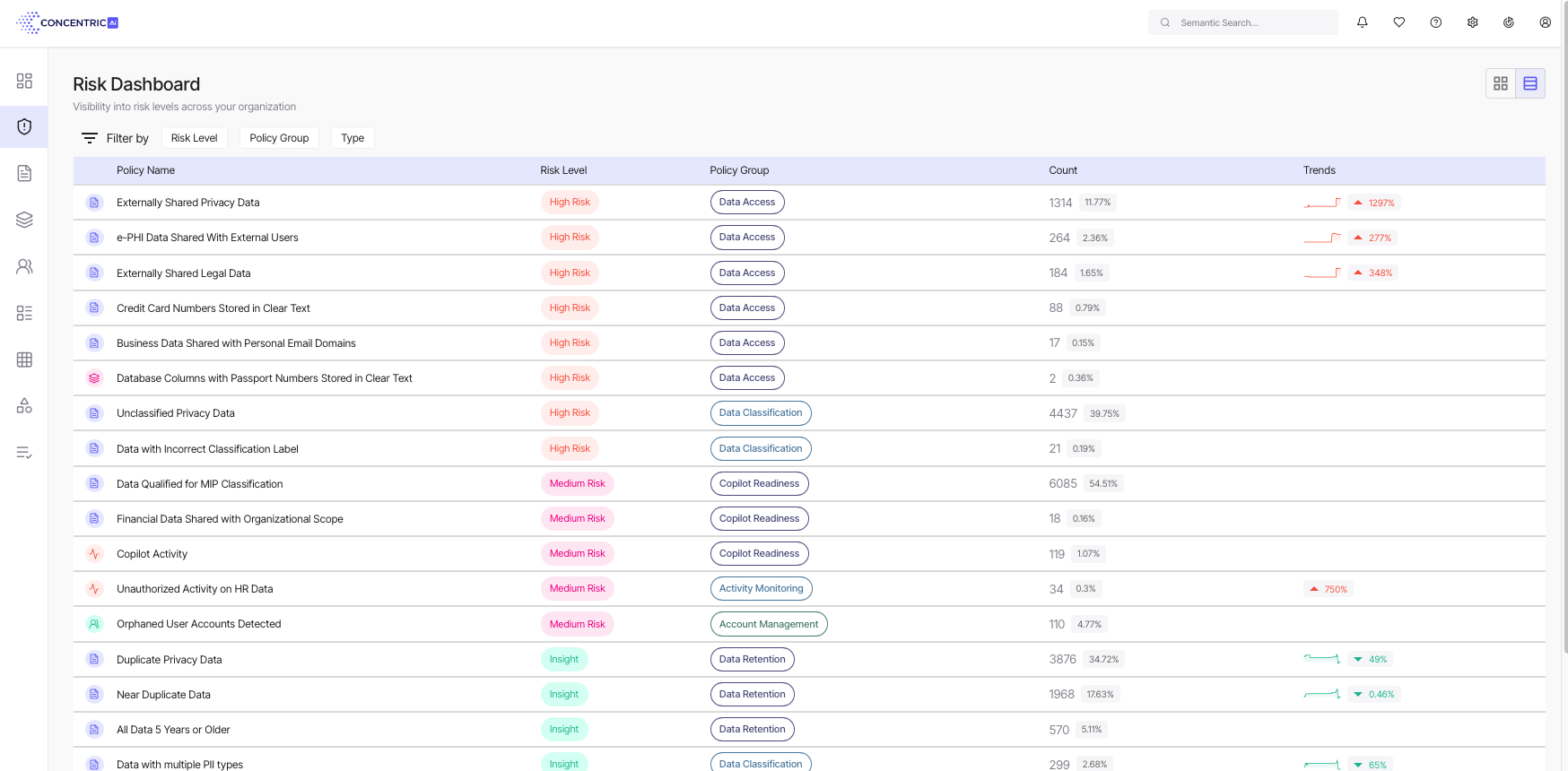
The Semantic Intelligence “Risk Dashboard” provides an at-a-glance view of data at risk across your organization. Risks are listed according to the threat they pose, and users can filter by risk level (High, Medium, and Insight), risk type, or policy group.
Generative AI: A Double-Edged Sword
The rise of generative AI has exponentially complicated this landscape. While these tools offer unprecedented productivity gains, they also present significant data security risks.
Consider the dual threat: First, direct data leakage when employees upload sensitive corporate information to public AI platforms. Second, the more insidious risk of AI models permanently incorporating and learning from uploaded data.
“Once these models train on your data, you can say goodbye,” Krishnan warns. “They’re never going to forget, and that data is now in the public domain for everyone to access.”
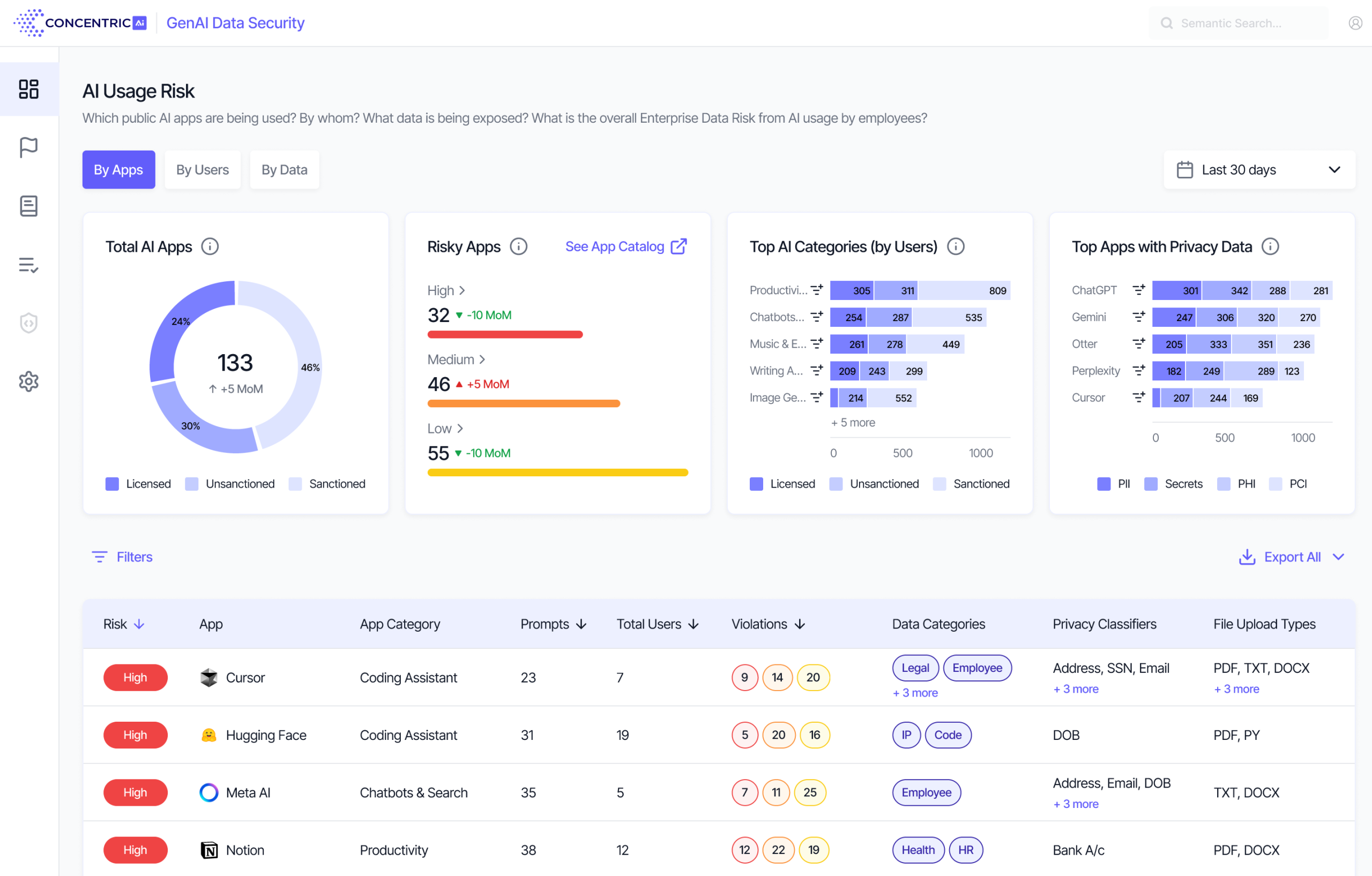
The Semantic Intelligence platform gives full visibility into which public GenAI apps users are accessing, including shadow GenAI, and indicates your overall risk from these apps.
A Holistic Approach to Data Security
Concentric AI’s solution represents a paradigm shift. By leveraging deep learning and advanced language models, the company has developed a platform that provides context-aware data security across multiple dimensions. Their approach goes beyond traditional classification. The platform can:
- Identify sensitive data across structured and unstructured environments
- Monitor data risks across on-premises and cloud systems
- Manage permissions with granular precision
- Detect and remediate risks across 10 different dimensions
“We’re the only ones offering a comprehensive spectrum of data security governance,” Krishnan emphasizes.
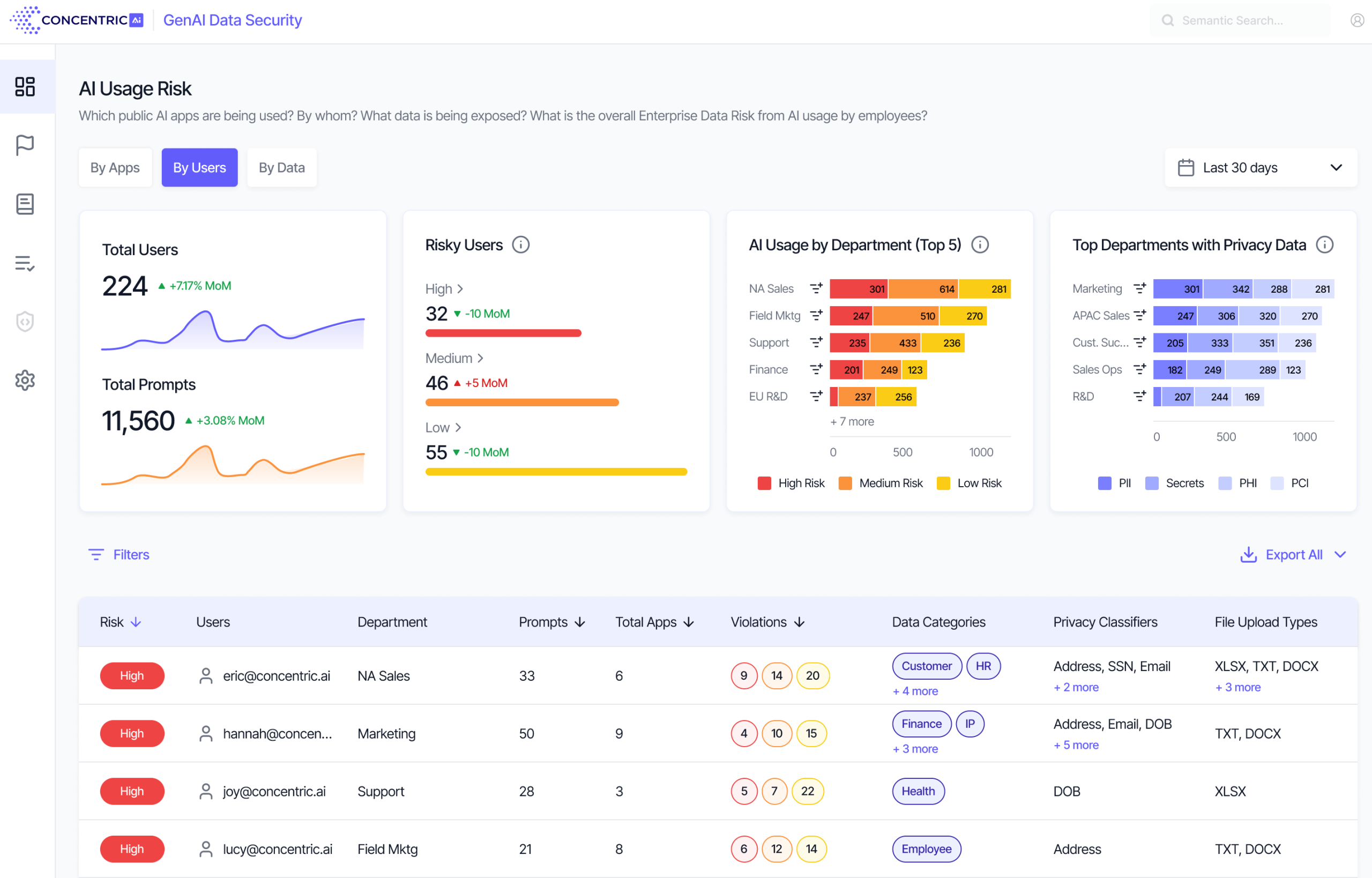
Semantic Intelligence gives you full visibility into which users are accessing public GenAI applications, including their department, and indicates overall risk from these users.
The CISO’s New Mandate
For Chief Information Security Officers, this means reimagining data protection strategies. No longer can security be a reactive, checkbox exercise. It must become a proactive, intelligence-driven discipline. The call to action is clear: Implement a holistic data security governance program that can:
- Understand data contextually
- Monitor data in motion
- Prevent unauthorized access and sharing
- Protect against generative AI-related risks
Practical Steps Forward
- Conduct a comprehensive data discovery audit
- Implement context-aware DLP solutions
- Create clear policies for generative AI tool usage
- Continuously monitor and adapt security strategies
The Numbers Tell the Story
Concentric AI’s approach isn’t theoretical. They’ve already helped hundreds of customers, ranging from tens of terabytes to over 30 petabytes of data, operationalize data security at scale.
“For the first time,” Krishnan says, “enterprises can actually understand and protect their most critical asset without overwhelming their security teams.”
Looking Ahead
As generative AI continues to evolve, so too must our approach to data security. The organizations that will thrive are those willing to embrace innovative, context-aware solutions that go beyond traditional governance models. The future of cybersecurity isn’t about building higher walls. It’s about developing smarter, more adaptive protection mechanisms that understand data’s inherent complexity.
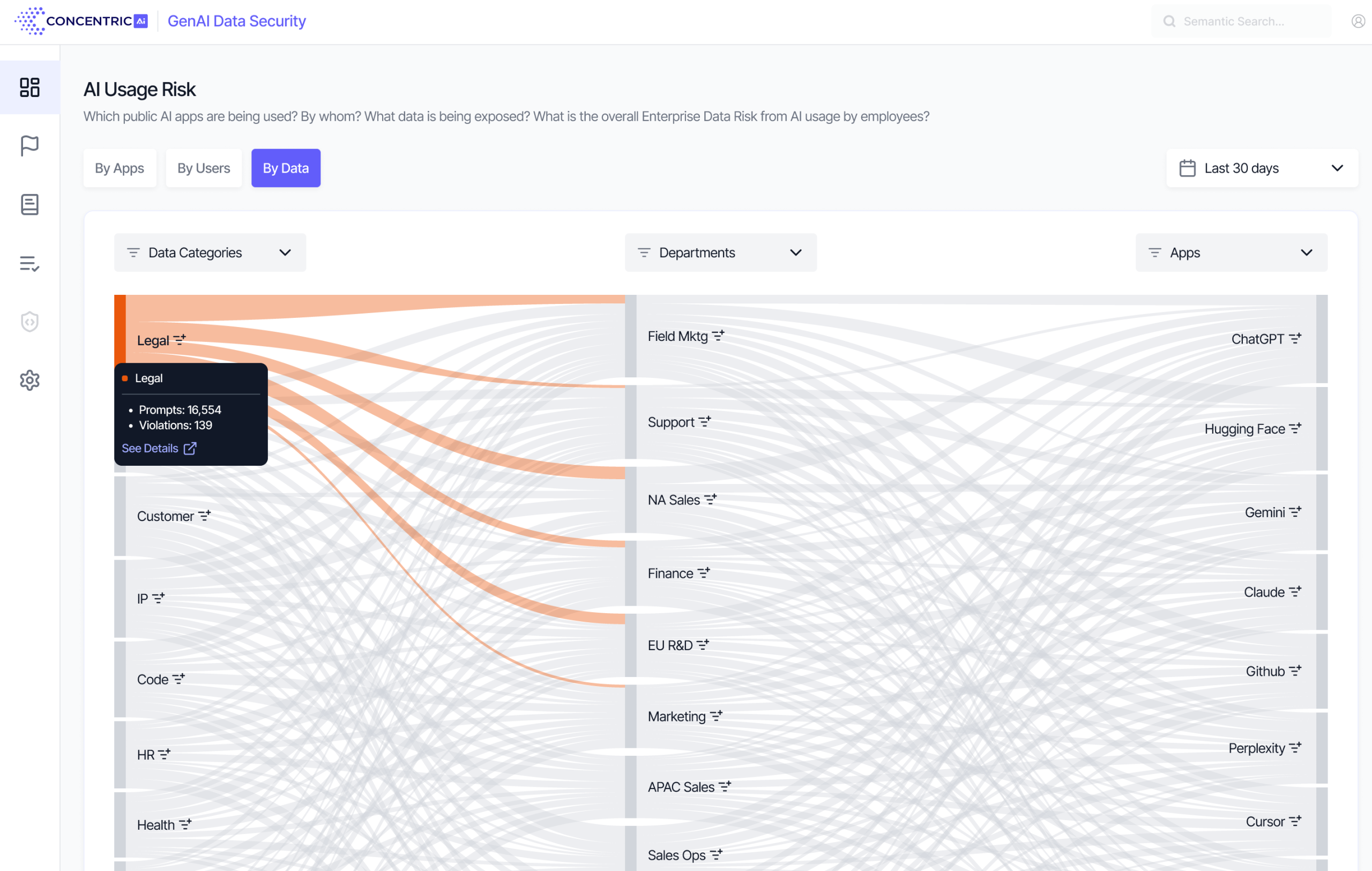
Semantic Intelligence gives you full visibility into what type of data is being shared with each GenAI application, by department.
Concentric AI at Black Hat USA 2025
Concentric AI announced it will showcase enterprise data protections across GenAI use cases at Black Hat USA 2025, highlighting new capabilities to discover “shadow GenAI” and safeguard data when employees interact with public GenAI tools. These additions reinforce the need for data security that moves beyond rules and regex to understand context at scale.
The company’s update follows recent acquisitions of Swift Security and Acante, combining DSPM, DLP, and GenAI governance into a single platform spanning structured, unstructured, and semi-structured data across cloud and on-prem environments.
Concentric’s Semantic Intelligence™ now emphasizes protection at rest, in motion, and in use, extending beyond proprietary assistants like Microsoft Copilot to monitor and prevent exfiltration via public GenAI tools and to enforce access governance for proprietary GenAI workloads. Practically, that means detecting unsanctioned GenAI usage, curating training data for approved models, and automatically correcting risky permissions – exactly the kinds of controls security leaders have struggled to operationalize with legacy approaches.
As CEO Karthik Krishnan notes, while GenAI offers efficiency and cost benefits, “it is essential to establish protections to prevent data leaks and ensure compliance.”
Call to Action
CISOs and security leaders: The time to act is now.
Don’t wait for the next data breach to modernize your approach. Explore solutions that provide comprehensive, context-aware data security governance. Your organization’s most valuable asset is counting on you.
Learn more at https://concentric.ai/
Author’s Note: This article is based on an exclusive interview with Karthik Krishnan, founder and CEO of Concentric AI, at the 2025 Black Hat security conference in Las Vegas.
About the Author
 Pete Green is the CISO / CTO of Anvil Works, a ProCloud SaaS company and co-author of “The vCISO Playbook: How Virtual CISOs Deliver Enterprise-Grade Cybersecurity to Small and Medium Businesses (SMBs)”. With over 25 years of experience in information technology and cybersecurity, Pete is a seasoned and accomplished security practitioner.
Pete Green is the CISO / CTO of Anvil Works, a ProCloud SaaS company and co-author of “The vCISO Playbook: How Virtual CISOs Deliver Enterprise-Grade Cybersecurity to Small and Medium Businesses (SMBs)”. With over 25 years of experience in information technology and cybersecurity, Pete is a seasoned and accomplished security practitioner.
Throughout his career, he has held a wide range of technical and leadership roles, including LAN/WLAN Engineer, Threat Analyst, Security Project Manager, Security Architect, Cloud Security Architect, Principal Security Consultant, Director of IT, CTO, CEO, Virtual CISO, and CISO.
Pete has supported clients across numerous industries, including federal, state, and local government, as well as financial services, healthcare, food services, manufacturing, technology, transportation, and hospitality.
He holds a Master of Computer Information Systems in Information Security from Boston University, which is recognized as a National Center of Academic Excellence in Information Assurance / Cyber Defense (CAE IA/CD) by the NSA and DHS. He also holds a Master of Business Administration in Informatics.