Security experts at Cisco Talos have discovered a new strain of the Fareit Info stealer that uses a different File hash for each attack to avoid AV Detection
Security experts at the Cisco Talos team have detected a new strain of the Fareit malware. Fareit is an info stealer that has been around since 2012, it is usually used to breach a computer and download other malware on the infected system. As explained by the researchers at Cisco, Fareit has evolved over the time, it was initially used only as a malware downloader, but over the time is was specialized in data exfiltration, mainly in extracting passwords from the victims’ browsers.
In May 2013, Fareit was used as downloader in a watering hole attacks based the well-known exploit kit Blackhole against the Indian gov Web site. In April 2015, the security experts at the Fidelis Cybersecurity firm have discovered a new variant of the Pushdo spamming botnet, which infected machines in more than 50 countries worldwide. The botnet is able to send out around 7.7 billion spam messages per day. The greatest number of infections was located in India, Indonesia, Turkey and Vietnam, the latest version of the Pushdo botnet was used by crooks to spread several strains of malware, including the Fareit data stealer, Cutwail spam malware and online banking menaces such as Dyre and Zeus.
Earlier this year, criminals were changing DNS entries to redirect unsuspecting users to domains hosting the Fareit malware
What’s new in this last Fareit campaign?
The new version of the Fareit malware is able to change its file hash with each infection, even if the file name remains the same. The author of the malware implemented this feature to avoid detection of antivirus software.
“This makes it very difficult to track them. Many detection tools in the security community rely on a hash-based search and correlation algorithms. It is interesting that they are frequently reusing similar filenames, but making such an effort to make sure most samples have an unique hash. ” states the blog post published by Cisco Talos. “One possible reason for this might be, that the mechanism which they use to download additional malware files or modules (e.g. cclub02.exe), need fixed names or paths (like http://IP/cclub02.exe) and is not flexible enough to handle on-the-fly generated file names on a per victim/campaign base,” This could also indicate a pay-per-infection botnet, but of course, this is speculation until we reverse engineer the local binaries and analyze the server command and control software.”
The expert noticed suspicious executables that downloaded files by using the following URLs in one of their customer networks.
- http://89.144.2.119/cclub02.exe
- http://89.144.2.115/cclub02.exe
Cisco’s security products recorded 2,455 Fareit samples, but only 23 of them shared the same hash. Digging deeper into the data, they’ve also noticed that
All the samples detected by the researchers communicated with the above two C&C servers (hosted at 89.144.2.115 and 89.144.2.119), despite 2,455 samples contacted the 89.144.2.115 URL only 23 of these samples shared the same hash, the rest were unique samples.
The situation was quite equivalent to the C&C server located at 89.144.2.119.
“The interesting part is many of those samples tried to download files with filenames similar to the ones previously discussed. This shows that adversaries are attempting to bypass hash and signature based detection methods by ensuring their samples are unique per attack or campaign.”
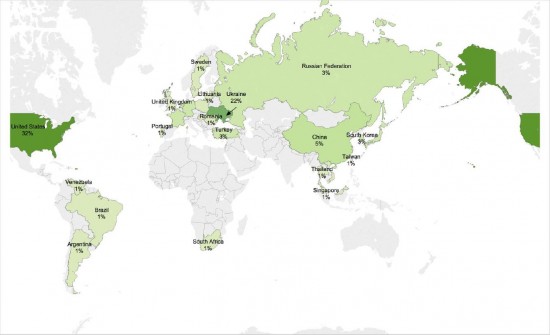
Checking the geolocation of these IPs addresses related to the infections it is possible to note that the top countries are US, Ukraine, and China.
The experts explained that Fareit sample detection was low in VirusTotal, most of the binary files infected with the malware have an average score of 4/56.
Who is behind the attack?
The evidence collected by the security experts led them to believe that this Fareit campaign is run by a single group.
It is curious that despite criminals are making an effort to generate malware with different hashes, they are reusing the same or similar file names.
“This makes them easily trackable by simple string matches on these filenames and their derivatives. Happy hunting.”