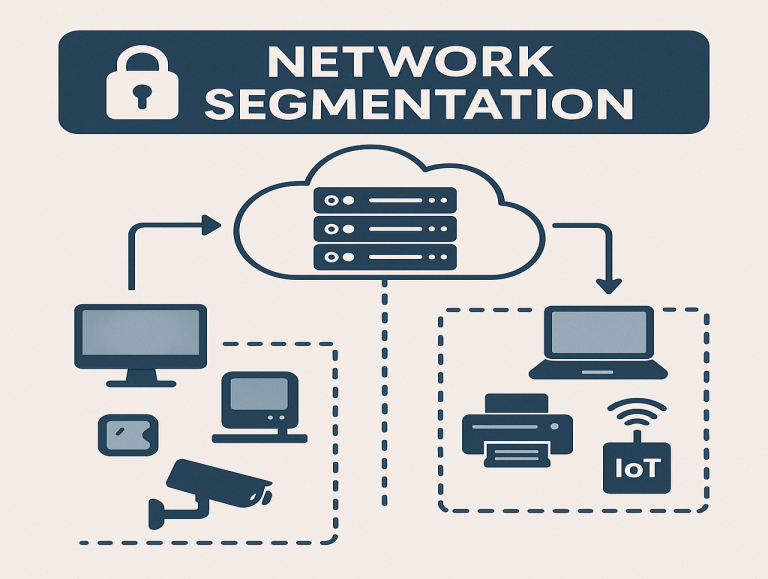
Let’s start with a simple truth: Most organizations don’t need more cybersecurity tools. The reality is that businesses require better boundaries in 2025 to restrict access to critical sensitive corporate data.
Every week I run into IT leaders who invest a significant amount of their budgets in firewalls, antivirus, and threat detection tools—yet their internal networks remain wide open and vulnerable to attack. One compromised device—a printer, a fridge, a laptop—will allow cybercriminals to move laterally across the entire environment. Employees may also have open access to what should be restricted files and systems.
Why? Because everything’s on the same flat network with no segmentation. Nothing is isolated and there’s no plan for limiting access and protecting different types of systems and files.
You wouldn’t allow employees free access to your HR records or let just anyone walk into your server room. So why not protect your network in a similar manner?
Defining Network Isolation
It’s more than an industry buzzword. Network isolation creates control over data flow, access, and how far a compromise can spread. At its core, this approach sets clear, enforceable limits between your systems, apps, users, and devices.
What does that look like?
· Segmentation splits the network into zones based on departmental, technological, regulatory compliance and other data protection requirements. For example, the company could establish different rules for finance, human resources, accounting, guest Wi-Fi, and IoT devices. Some guidelines may overlap, but establishing the proper segmentation policies and implementing effective systems and tools is critical.
· Microsegmentation limits access inside each zone down to the individual workloads.
· Isolation is the guiding principle: systems should only connect when absolutely necessary, with access properly limited and monitored – and easily revocable.
Done right, segmentation is invisible to network users, reduces traffic noise, and improves performance. However, its real value is in stopping threats from spreading and buying IT teams time to respond when something goes wrong (like a device breach).
Network isolation can be created two different ways. Most organizations often require both options to maximize data protection capabilities and minimize system disruptions, and those methodologies include:
· Physical Segmentation: This old-school method employs separate hardware and cabling. While this approach is simple and reliable—it’s also rigid and costly.
· Virtual Segmentation: Leveraging VLANs and access controls to carve up shared infrastructure. Flexible, scalable, and much easier to deploy in modern environments.
Segmentation is Mission-Critical
Flat networks are dangerous. While your organization might have strong perimeter tools in place, once someone or something gets inside, it’s open season if no segmentation exists. There is little to stop
cybercriminals from accessing every system and file once they’ve made a successful breach of your outer defenses.
Here are some of the things at risk with that cybersecurity approach.
· Lateral movement: One infected device allows invaders to scan and access everything.
· Malware spread: Ransomware thrives on flat networks—it moves fast and hits hard.
· Lack of visibility: When every system is connected and shares information freely, it’s hard to trace the source of a breach.
· Security overcompensation: Buying more tools to compensate for poor architecture is wasteful and ineffective. This approach appropriates funds that could be invested in growing the business and improving the customer experience.
Most companies don’t suffer a breach because they lack cybersecurity tools, but due to missing boundaries. A segmented, isolated network fixes those issues. A compromised device stays contained since it cannot access other systems, servers and users. Malware simply hits a wall—it can’t spread outside its zone.
Network segmentation provides your team with clarity about what’s talking to what, and why, and reduces your reliance on perimeter defenses. It’s not just a safer approach, but a more effective way to protect systems, data, and people. According to a recent Akamai survey, 93% of IT security decision-makers agree that segmentation is critical to thwarting damaging attacks. Other research highlights benefits such as improved workflows, stronger collaboration capabilities, and faster incident response times.
How to Get Started (Without Starting Over)
The good news is organizations don’t need to rebuild their networks from scratch to enjoy the security of segmentation. You simply need to:
1. Map all assets. Take a full inventory of your devices, applications and data flows, including anything that lies outside the common IT infrastructure. For example, if your smart fridge is on the same VLAN as your finance system, document and highlight that connection.
2. Identify natural boundaries. Group (or segment) by department, access level, device type and third-party connections.
3. Use existing tools. If the organization already has VLANs, firewalls and access lists—identify and incorporate them into the new ecosystem. You may not need a new platform, just a better configuration.
4. Test and iterate. Segmentation is not a “set it and forget it” process, but a dynamic methodology that requires periodic updates. Monitor traffic to see what breaks and fix it and make other improvements whenever possible.
5. Seek assistance. You don’t need a network engineer to implement segmentation — but having one will help. The right technology partner can prevent expensive missteps and ensure your architecture is secured much faster.
Start Small
Flat networks are convenient—until they’re not. Segmentation allows organizations to limit the damage of cybersecurity attacks, slow the spread and give your team time to respond when everything goes sideways.
Perfect architecture is not required to make progress. Start where time and budget allows, investing in the steps that will help define boundaries, eliminate vulnerabilities and reduce exposure. Then build from there.
Develop and execute on a long-term network segmentation plan that ensures continual improvement. Commitment is critical – since hope is not an effective strategy (but smart design is).
About the Author
 James Coberly is Chief Technology Officer at Massive Networks. He leverages more than 35 years of experience in senior engineering, management, and technological innovation in the telecommunications, networking, and connectivity sectors. His leadership has driven Massive Networks to shift its value proposition from a commodity-based carrier model to a networking services offering focused on superior connectivity, high performance, and end-user success. He has led multi-national teams, creating transformative communications technologies and services. James has contributed his technical skills to companies such as Vulcan Microsystems, OpSys, and Defense Technology (DEF-TEC), including consulting work for household-name organizations like Microsoft, The Miami HEAT, and Carnival Cruise Lines. James can be reached online at [email protected], https://x.com/Massive1Network, https://www.linkedin.com/company/massive-networks/ and at www.massivenetworks.com.
James Coberly is Chief Technology Officer at Massive Networks. He leverages more than 35 years of experience in senior engineering, management, and technological innovation in the telecommunications, networking, and connectivity sectors. His leadership has driven Massive Networks to shift its value proposition from a commodity-based carrier model to a networking services offering focused on superior connectivity, high performance, and end-user success. He has led multi-national teams, creating transformative communications technologies and services. James has contributed his technical skills to companies such as Vulcan Microsystems, OpSys, and Defense Technology (DEF-TEC), including consulting work for household-name organizations like Microsoft, The Miami HEAT, and Carnival Cruise Lines. James can be reached online at [email protected], https://x.com/Massive1Network, https://www.linkedin.com/company/massive-networks/ and at www.massivenetworks.com.