Page 38 - Cyber Defense eMagazine September 2025
P. 38
• Harvest Today, Decrypt Later
Cybercriminals think long-term. They are well aware that quantum computing is still some time away. But
that doesn’t stop them from stealing encrypted information. Why? They will store it securely until quantum
computing becomes readily available; then they will decrypt it. The impending arrival of quantum
computers has set the cat amongst the pigeons. Cybercriminals can’t wait to score a huge payday later,
making concerted efforts today.
• Impact on Blockchain
Blockchain is not unhackable, but it is difficult to hack. A bunch of cryptographic algorithms keep it secure.
These include SHA-256 (Secure Hash Algorithm 256-bit) and ECDSA (Elliptic Curve Digital Signature
Algorithm). Today, cybercriminals might not attempt to target blockchains and steal crypto. But tomorrow,
with the availability of a quantum computer, the crypto vault can be broken into, without trouble.
• Wide Gap Between Cybersecurity Posture and Attacks
We keep saying that quantum computing and quantum computing-enabled threats are still some time
away. And, this is true. But when the technology is here, it will evolve and gain traction. The attacks will
also evolve accordingly. The raw computation power of quantum machines will ensure that encryption
can be broken easily. Forging digital signatures, decrypting secure communication, or accessing and
decrypting critical information will be a breeze. You therefore need to start upgrading your security
systems to future-proof them. Otherwise, you will be caught in a vicious cycle of playing catch-up.
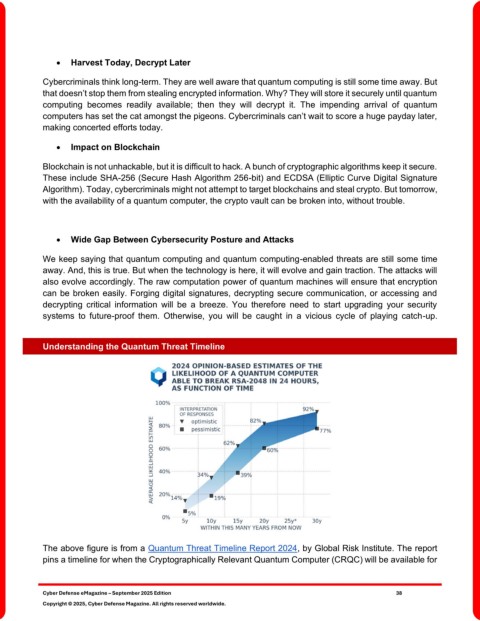
Understanding the Quantum Threat Timeline
The above figure is from a Quantum Threat Timeline Report 2024, by Global Risk Institute. The report
pins a timeline for when the Cryptographically Relevant Quantum Computer (CRQC) will be available for
Cyber Defense eMagazine – September 2025 Edition 38
Copyright © 2025, Cyber Defense Magazine. All rights reserved worldwide.