Page 230 - Cyber Defense eMagazine September 2025
P. 230
Healthcare: Electronic Health Records (EHRs) and PHI are often protected by ECC-based security.
Quantum compromise would expose patient identities, diagnoses, and histories, ripe for exploitation or
blackmail.
Intellectual Property: Corporations could have trade secrets and patent applications stolen before filing,
allowing competitors to replicate and deploy them first.
Critical Infrastructure: Power grids and water systems rely on PKI for SCADA system commands. A
quantum-empowered attacker could feasibly disrupt these at scale, causing cascading failures in
essential services.
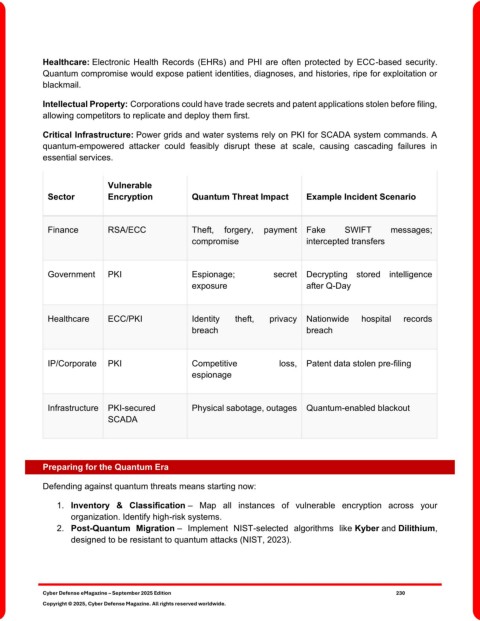
Vulnerable
Sector Encryption Quantum Threat Impact Example Incident Scenario
Finance RSA/ECC Theft, forgery, payment Fake SWIFT messages;
compromise intercepted transfers
Government PKI Espionage; secret Decrypting stored intelligence
exposure after Q-Day
Healthcare ECC/PKI Identity theft, privacy Nationwide hospital records
breach breach
IP/Corporate PKI Competitive loss, Patent data stolen pre-filing
espionage
Infrastructure PKI-secured Physical sabotage, outages Quantum-enabled blackout
SCADA
Preparing for the Quantum Era
Defending against quantum threats means starting now:
1. Inventory & Classification – Map all instances of vulnerable encryption across your
organization. Identify high-risk systems.
2. Post-Quantum Migration – Implement NIST-selected algorithms like Kyber and Dilithium,
designed to be resistant to quantum attacks (NIST, 2023).
Cyber Defense eMagazine – September 2025 Edition 230
Copyright © 2025, Cyber Defense Magazine. All rights reserved worldwide.