Page 78 - Cyber Defense eMagazine - October 2017
P. 78
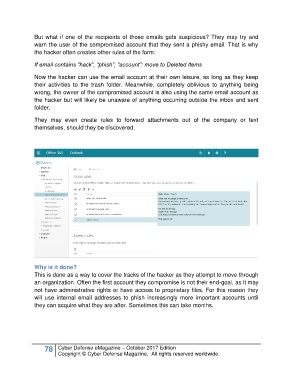
But what if one of the recipients of those emails gets suspicious? They may try and
warn the user of the compromised account that they sent a phishy email. That is why
the hacker often creates other rules of the form:
If email contains “hack”, “phish”, “account”: move to Deleted Items
Now the hacker can use the email account at their own leisure, as long as they keep
their activities to the trash folder. Meanwhile, completely oblivious to anything being
wrong, the owner of the compromised account is also using the same email account as
the hacker but will likely be unaware of anything occurring outside the inbox and sent
folder.
They may even create rules to forward attachments out of the company or text
themselves, should they be discovered.
Why is it done?
This is done as a way to cover the tracks of the hacker as they attempt to move through
an organization. Often the first account they compromise is not their end-goal, as it may
not have administrative rights or have access to proprietary files. For this reason they
will use internal email addresses to phish increasingly more important accounts until
they can acquire what they are after. Sometimes this can take months.
78 Cyber Defense eMagazine – October 2017 Edition
Copyright © Cyber Defense Magazine, All rights reserved worldwide.