Page 56 - Cyber Defense eMagazine - October 2017
P. 56
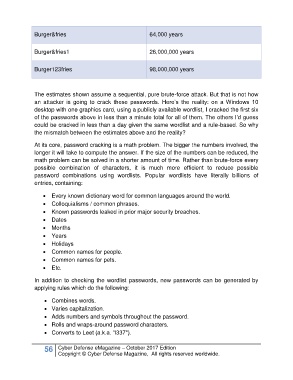
Burger&fries 64,000 years
Burger&fries1 26,000,000 years
Burger123fries 98,000,000 years
The estimates shown assume a sequential, pure brute-force attack. But that is not how
an attacker is going to crack these passwords. Here’s the reality: on a Windows 10
desktop with one graphics card, using a publicly available wordlist, I cracked the first six
of the passwords above in less than a minute total for all of them. The others I’d guess
could be cracked in less than a day given the same wordlist and a rule-based. So why
the mismatch between the estimates above and the reality?
At its core, password cracking is a math problem. The bigger the numbers involved, the
longer it will take to compute the answer. If the size of the numbers can be reduced, the
math problem can be solved in a shorter amount of time. Rather than brute-force every
possible combination of characters, it is much more efficient to reduce possible
password combinations using wordlists. Popular wordlists have literally billions of
entries, containing:
• Every known dictionary word for common languages around the world.
• Colloquialisms / common phrases.
• Known passwords leaked in prior major security breaches.
• Dates
• Months
• Years
• Holidays
• Common names for people.
• Common names for pets.
• Etc.
In addition to checking the wordlist passwords, new passwords can be generated by
applying rules which do the following:
• Combines words.
• Varies capitalization.
• Adds numbers and symbols throughout the password.
• Rolls and wraps-around password characters.
• Converts to Leet (a.k.a. “l337").
56 Cyber Defense eMagazine – October 2017 Edition
Copyright © Cyber Defense Magazine, All rights reserved worldwide.