Page 81 - Cyber Defense eMagazine June 2020 Edition
P. 81
The devil lives the cloud
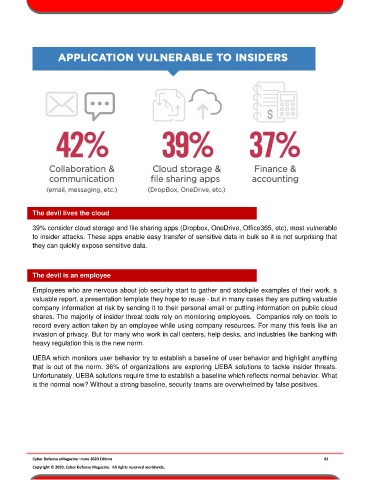
39% consider cloud storage and file sharing apps (Dropbox, OneDrive, Office365, etc), most vulnerable
to insider attacks. These apps enable easy transfer of sensitive data in bulk so it is not surprising that
they can quickly expose sensitive data.
The devil is an employee
Employees who are nervous about job security start to gather and stockpile examples of their work, a
valuable report, a presentation template they hope to reuse - but in many cases they are putting valuable
company information at risk by sending it to their personal email or putting information on public cloud
shares. The majority of insider threat tools rely on monitoring employees. Companies rely on tools to
record every action taken by an employee while using company resources. For many this feels like an
invasion of privacy. But for many who work in call centers, help desks, and industries like banking with
heavy regulation this is the new norm.
UEBA which monitors user behavior try to establish a baseline of user behavior and highlight anything
that is out of the norm. 36% of organizations are exploring UEBA solutions to tackle insider threats.
Unfortunately, UEBA solutions require time to establish a baseline which reflects normal behavior. What
is the normal now? Without a strong baseline, security teams are overwhelmed by false positives.
Cyber Defense eMagazine –June 2020 Edition 81
Copyright © 2020, Cyber Defense Magazine. All rights reserved worldwide.