Page 66 - Cyber Defense eMagazine June 2020 Edition
P. 66
The onus is on you to establish the context before beginning to understand and prioritize the risk, then
ultimately address the vulnerabilities.
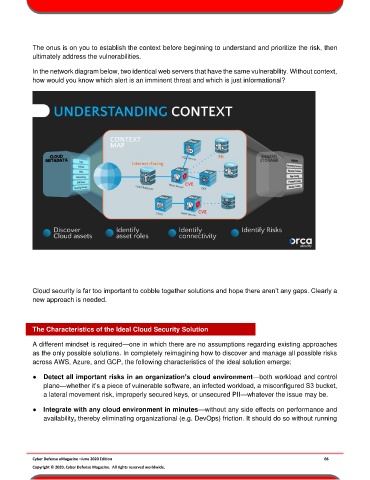
In the network diagram below, two identical web servers that have the same vulnerability. Without context,
how would you know which alert is an imminent threat and which is just informational?
Cloud security is far too important to cobble together solutions and hope there aren’t any gaps. Clearly a
new approach is needed.
The Characteristics of the Ideal Cloud Security Solution
A different mindset is required—one in which there are no assumptions regarding existing approaches
as the only possible solutions. In completely reimagining how to discover and manage all possible risks
across AWS, Azure, and GCP, the following characteristics of the ideal solution emerge:
● Detect all important risks in an organization’s cloud environment—both workload and control
plane—whether it’s a piece of vulnerable software, an infected workload, a misconfigured S3 bucket,
a lateral movement risk, improperly secured keys, or unsecured PII—whatever the issue may be.
● Integrate with any cloud environment in minutes—without any side effects on performance and
availability, thereby eliminating organizational (e.g. DevOps) friction. It should do so without running
Cyber Defense eMagazine –June 2020 Edition 66
Copyright © 2020, Cyber Defense Magazine. All rights reserved worldwide.