Page 61 - Cyber Warnings August 2017
P. 61
to use Tor for such a purpose. Finally, if we are anonymous and private – there would be a
great chance that we would be secure as well. In this case – we are not talking about the bad
guys who are usually the target of many investigations, but rather about the common people
who would use Tor for, say, family purposes and who would want to offer the best possible
security to their loving ones. In those cases – we can say that those people are anonymous,
private and secure at the same glance.
Tor’s encryption concept
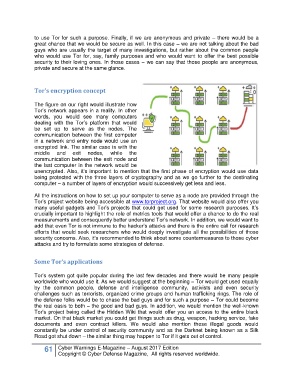
The figure on our right would illustrate how
Tor’s network appears in a reality. In other
words, you would see many computers
dealing with the Tor’s platform that would
be set up to serve as the nodes. The
communication between the first computer
in a network and entry node would use an
encrypted link. The similar case is with the
middle and exit nodes, while the
communication between the exit node and
the last computer in the network would be
unencrypted. Also, it’s important to mention that the first phase of encryption would use data
being protected with the three layers of cryptography and as we go further to the destinating
computer – a number of layers of encryption would successively get less and less.
All the instructions on how to set up your computer to serve as a node are provided through the
Tor’s project website being accessible at www.torproject.org. That website would also offer you
many useful gadgets and Tor’s projects that could get used for some research purposes. It’s
crucially important to highlight the role of metrics tools that would offer a chance to do the real
measurements and consequently better understand Tor’s network. In addition, we would want to
add that even Tor is not immune to the hacker’s attacks and there is the entire call for research
efforts that would seek researchers who would deeply investigate all the possibilities of those
security concerns. Also, it’s recommended to think about some countermeasures to those cyber
attacks and try to formulate some strategies of defense.
Some Tor’s applications
Tor’s system got quite popular during the last few decades and there would be many people
worldwide who would use it. As we would suggest at the beginning – Tor would get used equally
by the common people, defense and intelligence community, activists and even security
challenges such as terrorists, organized crime groups and human trafficking rings. The role of
the defense folks would be to chase the bad guys and for such a purpose – Tor could become
the real oasis to both – the good and bad guys. In addition, we would mention the well-known
Tor’s project being called the Hidden Wiki that would offer you an access to the entire black
market. On that black market you could get things such as drug, weapon, hacking service, fake
documents and even contract killers. We would also mention these illegal goods would
constantly be under control of security community and as the Darknet being known as a Silk
Road got shut down – the similar thing may happen to Tor if it gets out of control.
61 Cyber Warnings E-Magazine – August 2017 Edition
Copyright © Cyber Defense Magazine, All rights reserved worldwide.