Page 37 - Cyber Defense eMagazine RSAC Special Edition 2025
P. 37
Cloud adoption and a hybrid work workforce significantly benefit organizations in terms of business
scalability and continuity, as well as employee productivity and satisfaction. However, they also introduce
unique challenges, such as data privacy, access security, compliance, and connectivity.
As businesses expand their digital footprint, cyber attackers increasingly target unsecured cloud
resources and remote endpoints. Traditional perimeter-based network and security architectures are not
capable of protecting distributed environments. Therefore, organizations must adopt a holistic, future-
proof network and cybersecurity architecture to succeed in this rapidly changing business landscape.
The Challenges
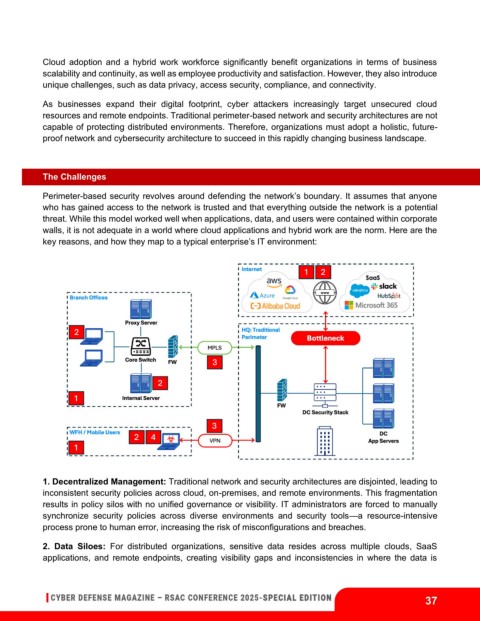
Perimeter-based security revolves around defending the network’s boundary. It assumes that anyone
who has gained access to the network is trusted and that everything outside the network is a potential
threat. While this model worked well when applications, data, and users were contained within corporate
walls, it is not adequate in a world where cloud applications and hybrid work are the norm. Here are the
key reasons, and how they map to a typical enterprise’s IT environment:
1. Decentralized Management: Traditional network and security architectures are disjointed, leading to
inconsistent security policies across cloud, on-premises, and remote environments. This fragmentation
results in policy silos with no unified governance or visibility. IT administrators are forced to manually
synchronize security policies across diverse environments and security tools—a resource-intensive
process prone to human error, increasing the risk of misconfigurations and breaches.
2. Data Siloes: For distributed organizations, sensitive data resides across multiple clouds, SaaS
applications, and remote endpoints, creating visibility gaps and inconsistencies in where the data is
37