A Cybersecurity Student’s First Time Experience with DefCon, BlackHat, and The Diana Initiative
Annabelle Klosterman, Cybersecurity Reporter, Cyber Defense Magazine 
Earlier in August, I experienced my first Hacker Summer Camp – three cybersecurity conferences that ran from August 10th to August 14th. While I didn’t make my way to BSidesLV, I attended The Diana Initiative, BlackHat, and DefCon in what turned out to be a whirlwind of a week. From preparing to go through walking the conference floor, I found the whole experience to be an invaluable part of my experience in cybersecurity.
Preparing
Having never been to multiple large-scale cybersecurity conferences within a short time frame, I didn’t know what to expect. Even prepping for the conference and trying to come up with a game plan was overwhelming. I watched previous recordings, joined the DefCon Discord community, and did some research on the conferences.
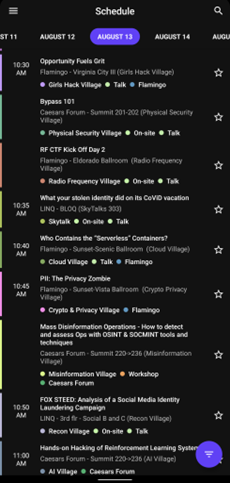
Taking advice from previous attendees, I decided to come up with a list of key items I wanted to get out of the conferences. With so many things going on, it’s difficult to do everything, so I knew going into it that I had to pick and choose what to try. I was also advised to not make recorded presentations a priority, as they could always be rewatched later.
With all this in mind, I carefully looked at the schedules for the various conference activities so I could make a rough plan to try and follow. However, as I continued to join communities and network with other professionals, I began to find more people I wanted to try and meet. I slowly began adjusting my schedule accordingly to set up meetings and lunches. I created a rough schedule that I could try and follow but knew that things might change so I kept things as flexible as they could be. As the conferences approached, I was ready to dive in and immerse myself.
Game Day(s)
The Diana Initiative – August 10-11
I started by going to The Diana Initiative where Jen Easterly, the Director of the Cybersecurity and Infrastructure Security Agency (CISA), was the keynote speaker. Additionally, I had the opportunity to listen to my dear friend Weijia Yan, share her journey through tech. The Diana Initiative also had a Surface Mount Device (SMD) workshop where I soldered a small heart-shaped circuit board. When turned on, the device had lights that blinked.

Overall, this was a great conference with a smaller feel that allowed for a more hands-on, discussion, and participatory approach in the presentations and workshops. It was wonderful to be surrounded by those who are working to build a more diverse and inclusive community that is welcoming to myself and others. It is inspiring to be a part of communities and initiatives like these that are trying to build a better future.
BlackHat – August 10-11

Walking into the venue for BlackHat, I immediately knew it was going to be a massive conference and completely different from the Diana Initiative. There was a giant BlackHat sign surrounded by crowds walking to and from various sessions. Every session room I saw had hundreds upon hundreds of seats. Throughout the two days, I was able to sit in on a few presentations, spend hours in the vendor hall, and check out some of the social hours hosted by companies.

For example, Matt Edmondson from Argelius Labs gave an insightful presentation titled Chasing Your Tail with a Raspberry Pi. I’ve always had a fascination with integrating physical security with cybersecurity, so I knew I could not pass this up. Matt demonstrated how he used off-the-shelf parts and wrote code to be able to determine if someone is physically being followed. It was interesting to learn about the various techniques and methodologies he implemented and I loved that he made it open source which you can check out for yourself here.

Another presentation worthy of noting is one titled Charged by an Elephant – An APT Fabricating Evidence to Throw You In Jail by Juan Andrés and Tom Hegel from SentinelOne. They showcased a threat actor’s activities that have taken place over more than a decade. What was especially interesting was learning the various ways they planted evidence that incriminated others. It was scary to learn how they discovered multiple other threat actors were targeting the same victims.
DefCon – August 11-14
This was the big conference, what everything had led up to, and by far the most overwhelming for me. There were so many things going on that even a couple of days in, I was still finding out that there were more things to do and check out. I could go on and on about everything I did and saw at DefCon but I’m assuming you don’t have hours to read so I’ll save you the time and just list a few of my favorite highlights.

One of the unique things about DefCon is that they have a track of presentations called Skytalks. Skytalks are presentations that are completely off the record – they do not allow cameras or recording. The room had roughly 300 seats and each chair was spaced a couple of feet apart so that the volunteers could ensure that individuals were not recording or on their devices. I had the opportunity to attend two of them – Geo-Targeting Live Tweets and Eradicating Disease with BioTerrorism.
I saw why Skytalks was a huge rage at the conference. A majority of the time, one would have to get in line an hour before the talk starts to get a spot. The trick I used was to try and go to the earliest Skytalk for that day. This proved to be successful since there weren’t as many people as some had stayed up late the night before (probably partying) and didn’t get up as early.

Some of the other presentations I learned from was one by the Co-Founder of Tor, Roger Dingledine. He explained How Russia is Trying to Block Tor and their techniques and how the Tor group reverse engineered their attempts which caused them to change their strategies and approach. James Pavur gave an insightful presentation on various radio frequency attacks that go on in outer space. He demonstrated how state and non-state actors can, and have, executed physical-layer attacks on satellite communications systems that have caused disruptions.

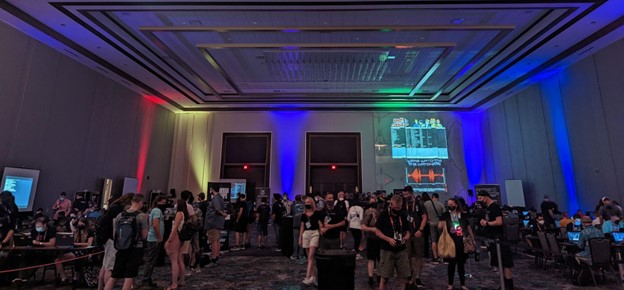
Another component of DefCon is the vast amount of villages they have. These villages contained talks, demonstrations, and typically a hands-on component where attendees could try their hand at it. For this year’s DefCon, they had 20+ villages. I was able to at least see every village but did not have time to try my hand at everything.
Of where I was able to spend time at the Biohacking Village, being able to see and understand the security behind some medical devices was rather interesting. They had multiple tables of various health care devices and demonstrations of how they worked. It was scary to think about how much damage an attacker could do if medical devices didn’t have proper security measures in place.

Aside from this, the Industrial Control Systems (ICS) Village was also fascinating! The Red Alert CTF within the ICS Village had a 3D model of a city and participants would try and gain access to the various control systems to make changes. There was also a Car Hacking Village with a couple of cars (including a Tesla) with attendees trying their hand at breaking and circumventing the security measures.

One of my favorite villages, though, was the Physical Security Village. They had a variety of different physical security components, including a mock keypad for a gated community, door locks, elevator doors, etc. I tried my hand at bypassing some of the door locks and loved learning about the mechanics and design behind everything.

In the end, DefCon was by far one of my favorite cybersecurity conferences I have ever attended. There were so many things to do and I know I didn’t cover even a quarter of them. I did my best to try and go to the hands-on villages over the presentations since those would be recorded. It was amazing to have a wide variety of topics, as there was something for everyone. Further, the community at DefCon was unlike any conference I had experienced. Despite the vast amount of attendees, it felt more customized, personable, and like a community than other conferences.
Networking
With thousands (easily 25k+ attendees) at these conferences, there were so many opportunities to meet industry leaders and others. Throughout the five days, I found that the Hacker Summer Camp is the time to meet most cybersecurity leaders in person. There were a few individuals and companies on my list, but there were others that I happened to run into or meet.
During the conferences, I had time to sit down and chat with Bob Ackerman. He founded Allegis Cyber – the world’s original cyber-focused venture firm. Shifting from a reactive to a proactive approach and consolidating companies within the industry are some of the things he foresees happening in the future. With artificial intelligence improving every day, he noted that the offensive capabilities will also be developed and is something to watch out for.
As he was talking about the state of cybersecurity, it was very apparent that Allegis Cyber has a deep understanding of everything cyber-related and that they know the entire cyber ecosystem. Bob noted that a lot of start-ups in the industry are concerned about navigating the entrepreneurial path while trying to have a successful company. It was insightful to hear his perspective on the industry and the problems he sees coming.
I had the opportunity to have lunch and meet Cyrus Robinson and Kris Brochhausen from Ingalls Information Security. They were also first-time attendees but I appreciated getting to hear about their journey and what they tried so far at the conferences. It was great to share experiences and also get some tips on what to check out at the conference.

Meeting the Founder of GirlsWhoHack, Bia, was amazing as well. She’s a 15-year-old, young woman who is striving to increase the number of girls in the cybersecurity field. I was inspired to find another young woman with similar goals and aspirations. We discussed potential collaboration between my outreach program, the Cyber Community Club (Cx3), and GirlsWhoHack.
Finally, I was able to meet and chat with Luke Potter, the Chief Operating Officer of CovertSwarm. They bring together every element of cybersecurity testing to help companies locate every security vulnerability they have. I was happy to share my thoughts and recommendations with Luke and Jack Smith as they’re in the process of creating an intern program for their company which people should keep an eye out for.
In addition to meeting new people, I was able to see some familiar faces. Reconnecting with students from activities and competitions I participated in and colleagues from my previous cybersecurity internships, made the environment come full circle. It was a wonderful time to meet others in person and see the cybersecurity community come together.
Reflecting
As a young cybersecurity student and professional, I was overwhelmed with everything the conferences had to offer. From presentations to workshops to villages, to networking opportunities, and so much more, the conferences had endless amounts of opportunities. The five days of conferences felt like so much but I learned to slow down and stop worrying about being able to attend everything.

Ultimately, I had a great experience with the Hacker Summer Camp and can’t wait to attend again. This time, I’ll be more prepared and ready to learn new things! There were so many wonderful people I met, and I learned more technically, but also personally, and professionally. I highly recommend that anyone who’s even slightly considering attending set aside the time and experience the conferences.
Tips + Advice
There are quite a few things I was thankful that I did that helped me make the most out of the conferences. I was glad I did research ahead of time and reached out to others for their advice. For those who plan on attending in the future, my top three tips are the following.
- Don’t try and do everything: There are far too many things and you won’t have enough time to do everything
- Hydrate and have comfortable shoes: It’s a lengthy few days with long walks, so try and stay in the best condition you can
- Prioritize properly: Take advantage of things you can only do at the conference
While those five days were some of the busiest days I’ve ever had, I learned and met a ton of those in the industry. It was an invaluable experience for me that I will remember for years. I truly appreciate the time and effort that the organizers, staff, volunteers, speakers, and attendees put in to make the conferences a success. Here’s to next year!
About The Author
 Annabelle Klosterman is a Cybersecurity Reporter for Cyber Defense Magazine (CDM) and CDM’s first Women in Cybersecurity scholarship awardee. She is a Cybersecurity Engineer for Southwest Airlines, Co-Founder/Program Director of the Cyber Community Club, and a Cyber Operations student at Dakota State University. Her areas of focus are offensive and defensive security, governance, risk and management, security consulting, program management, and cybersecurity training/outreach.
Annabelle Klosterman is a Cybersecurity Reporter for Cyber Defense Magazine (CDM) and CDM’s first Women in Cybersecurity scholarship awardee. She is a Cybersecurity Engineer for Southwest Airlines, Co-Founder/Program Director of the Cyber Community Club, and a Cyber Operations student at Dakota State University. Her areas of focus are offensive and defensive security, governance, risk and management, security consulting, program management, and cybersecurity training/outreach.
Throughout the years, Annabelle has competed in numerous competitions and placed second nationally at the Collegiate Cyber Defense Competition in 2022 and was a national finalist in CyberPatriot in 2019 and 2020. Additionally, she earned 1st place in the 2022 Idaho National Laboratory CyberCore CTF, and Women in Cybersecurity (WiCyS) CTF in 2021 and 2022. She holds SANS certifications in Cybersecurity Technologies (GFACT), Cloud Security (GCLD), and Incident Handling (GCIH).
Acknowledgments: Thank you to everyone who took the time to share their knowledge with me and to the organizers and volunteers at all three conferences. I’d like to give a special note of appreciation to the Women in Security and Privacy (WISP) for sponsoring my BlackHat pass and to the Cyber Defense Media Group for sponsoring my travels.





 We are in our 11th year, and Global InfoSec Awards are incredibly well received – helping build buzz, customer awareness, sales and marketing growth opportunities, investment opportunities and so much more.
We are in our 11th year, and Global InfoSec Awards are incredibly well received – helping build buzz, customer awareness, sales and marketing growth opportunities, investment opportunities and so much more.