By Avi Shua, CEO, and co-founder, Orca Security; former chief technologist at Check Point Software Technologies
Abstract: Humans are used to thinking in metaphors. While convenient, this limits our ability to innovate. Most cloud security solutions suffer from the same problem because they carry biases from the physical world. For cloud security to truly succeed, we need to stop iterating on tools designed for on-prem environments.
Look at your keyboard. That odd QWERTY layout dates back to the invention of the manual typewriter over 150 years ago. The keys were positioned in such a way to prevent the typebars from jamming on their way to striking the paper.
As technology advanced to computers, tablets, and smartphones, manufacturers continued to use the QWERTY keyboard layout. It’s crazy to think that 21st-century devices still carry the vestiges of a design from the mid-1800s.
The problem is that we tend to think in metaphors (e.g., “the PC is the new typewriter”). This limits the ability to truly innovate and leverage new capabilities as technology evolves. It happens all the time.
Unfortunately, the limitations of old tools can influence and constrain how we approach new problems. For software, this can lead to biased and suboptimal solutions for security, architecture, and performance. The consequences can be especially harsh when it comes to cybersecurity.
Lifting Physical Security Measures to the Cloud Is a Failed Strategy
Consider the days when on-premise datacenters were full of physical servers. To verify the security state of those machines, administrators had two options: run code on each via a software agent, or scan every system from the network to look for vulnerabilities, misconfigurations, and other risks. When businesses began to move their workloads to the cloud, these same security technologies were merely lifted and shifted.
Organizations ended up having both an agent – the same agent from the on-prem days bolted on to the cloud – as well as the same scanners. But those tools weren’t reimagined to support the unique characteristics of cloud computing, thus the limitations of agents and scanners were magnified on the new platform.
While agents can see everything that happens, they have to be installed on every machine to be scanned. This simply isn’t practical in a cloud environment that uses ephemeral servers, containers, and serverless workloads that burst into existence for a short time and then disappear just as quickly. No human—and perhaps not even automation tools—can keep track of software agents and ensure they’re consistently installed in such a dynamic environment. What’s more, the high cost and complexity of agent deployment and maintenance, as well as friction with DevOps teams, make agent-based scanning totally unsuitable for the cloud.
As for network scanners—which are essentially whitelisted hacking tools—visibility is critically limited to just those assets that are already known and accessible. Moreover, scans put data integrity at risk, use significant system resources during test procedures, and completely miss some assets and risks because they simply aren’t visible or accessible.
New Tools Address (Some) Cloud Security Needs
With legacy security tools leaving gaps, new cloud-native tools attempt to fill the need to assess risk in cloud estates. For example, Cloud Security Posture Managers (CSPMs) verify that cloud configurations are following security best practices and compliance standards such as the CIS framework, Azure and GCP benchmarks, and PCI DSS or HIPAA guidelines. While CSPMs do look at configurations unique to cloud environments, at best they provide shallow coverage because they don’t go inside machines, but rather view them from the outside.
Cloud platform hosts provide a number of security tools exclusive to their own environments. Amazon, Google, and Microsoft all offer tools/services to detect threats, analyze application security, investigate potential security issues, discover unprotected keys and sensitive data, identify non-compliance with security frameworks and regulations, and more. Third-party vendors also provide tools—many of them retread from the on-premise environment—in each of these areas.
The key issue with such tools is that they only provide a partial view into your cloud estate’s risks and vulnerabilities. An organization must deploy multiple tools or services to get the full picture, and even then it’s not a holistic view. Each tool performs its own vulnerability detection and getting them all to communicate with one another and provide a clear context regarding each finding is nearly impossible. The onus is on you to establish the context before beginning to understand and prioritize the risk, then ultimately address the vulnerabilities.
In the network diagram below, two identical web servers that have the same vulnerability. Without context, how would you know which alert is an imminent threat and which is just informational?
Cloud security is far too important to cobble together solutions and hopes there aren’t any gaps. Clearly a new approach is needed.
The Characteristics of the Ideal Cloud Security Solution
A different mindset is required—one in which there are no assumptions regarding existing approaches as the only possible solutions. In completely reimagining how to discover and manage all possible risks across AWS, Azure, and GCP, the following characteristics of the ideal solution emerge:
- Detect all important risks in an organization’s cloud environment—both workload and control plane—whether it’s a piece of vulnerable software, an infected workload, a misconfigured S3 bucket, a lateral movement risk, improperly secured keys, or unsecured PII—whatever the issue may be.
- Integrate with any cloud environment in minutes—without any side effects on performance and availability, thereby eliminating organizational (e.g. DevOps) friction. It should do so without running a single opcode on the customer environment and without sending a single packet—all while guaranteeing 100% coverage.
- Prioritize alerts based on all available data, while presenting a manageable number of alerts. It makes no sense to 1) have a vulnerability management agent notify about 1,000 workloads at risk due to vulnerabilities, then 2) have to go to a CSPM to assess whether there is a real attack vector involved, followed by 3) having to install another distinct agent-based antivirus solution to detect existing compromises. That approach doesn’t work. The ideal solution must deliver the functionality of multiple tools out of the box and provide context-based actionable alerts—not “security concerns by the kilo.”
A Breakthrough Technique for Deeper Cloud Inspection Across 100% of AWS, Azure, and GCP Assets
Any solution based on these characteristics must leverage the cloud computing paradigm and abandon the biases of the physical computing world. It can be achieved by embracing virtualization instead of devices as the premise of inspection.
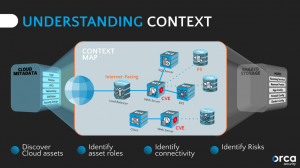
Today’s cloud datacenter separates storage devices and compute devices, connecting them via high-speed fiber optics. This enables a unique approach to deep cloud asset inspection. Through the proper configuration of privileges and roles, it’s possible to take a “snapshot” of an organization’s bits and bytes of block storage, rebuild a read-only image of the full environment on the side (i.e., out of band), then scan through the resulting image to look for risks and vulnerabilities.
This approach can see everything without the hassle of installing agents. It can scan the cloud configuration, network layout, and security configuration while reading into virtual machines’ disks, databases, and datastores, as well as logs for all of the cloud assets. It can analyze the data, build a full-stack inventory, and assess the security state of every discovered asset throughout the stack. All this, without impacting performance or availability.
Here is the real value of this approach: All of this information can be combined with contextual information from the cloud infrastructure to gain a context-aware view of the findings—the true level of risk. Context is important because it helps alleviate alert fatigue on behalf of the security team. Actionable findings can be immediately prioritized and assigned to security engineers or DevOps developers for mitigation or follow-up.
Upon completion of data analysis and reporting, the snapshot can simply be deleted without a trace. There is nothing to maintain or deprovision.
Legacy approaches to security have no place in the cloud. It takes a new mindset that is free from the past to envision innovative solutions for complete cloud security.
About the Author
 Avi Shua is the CEO and co-founder of Orca Security. He invented the patent-pending SideScanning™ technology upon which Orca Security is built. SideScanning™ uses a novel, out of band, zero impact integration with the cloud virtualization layer to gain full visibility into those risks that matter most—vulnerabilities, malware, misconfigurations, weak and leaked passwords, lateral movement risk and improperly secured customer data. Learn more at
Avi Shua is the CEO and co-founder of Orca Security. He invented the patent-pending SideScanning™ technology upon which Orca Security is built. SideScanning™ uses a novel, out of band, zero impact integration with the cloud virtualization layer to gain full visibility into those risks that matter most—vulnerabilities, malware, misconfigurations, weak and leaked passwords, lateral movement risk and improperly secured customer data. Learn more at
Company Website: – https://orca.security/
LinkedIn – https://www.linkedin.com/in/avishua/
Twitter – https://twitter.com/orcasec?s=20





 We are in our 11th year, and Global InfoSec Awards are incredibly well received – helping build buzz, customer awareness, sales and marketing growth opportunities, investment opportunities and so much more.
We are in our 11th year, and Global InfoSec Awards are incredibly well received – helping build buzz, customer awareness, sales and marketing growth opportunities, investment opportunities and so much more.