Informative sources on distributed denial of service (DDoS) attacks will often include at least one warning that nearly every website on the internet is a potential target. With the current ubiquity of DDoS attacks this is not a needlessly dire warning. Nearly every website is a potential target.
Yet there is a certain subset of website owners that might just assume these warnings don’t apply to them because their internet technology and online security knowledge is so far above that of the average website owner. Relatedly, there is also a certain subset of website owners that might just end up tremendously embarrassed when their websites go down to distributed denial of service attacks despite that impressive knowledge.
Widely distributed attacks
DDoS attacks are used to either slow a target website down to the point that it is no longer usable, or take the target offline altogether. Either way the end result of a successful attack is the same: the legitimate users of the website are denied its services while the attack is ongoing.
DDoS attacks are made possible by botnets, which are networks of internet-connected devices that have been infected by malware in order to allow attackers to control them remotely. Using the firepower of all these infected devices, the attacker can overwhelm the resources or use up the bandwidth of the target website.
These attacks have been an issue for websites and businesses for over 15 years and the issue is only getting bigger thanks to innovations like DDoS for hire services, DDoS ransom notes and massive Internet of Things (IoT) botnets. Successful attacks can now cost larger organizations anywhere from $20,000 and $100,000 per hour, and that isn’t factoring in the costs associated with the software damage that can accompany the attacks, the data breaches that can occur while DDoS attacks are used as a smokescreen, and the loss of user trust and loyalty that so often stems from DDoS-caused outages.
Even the experts
The past six months have seen a series of high-profile distributed denial of service attacks dominate headlines, not only because of the size of the attacks and the extent of their damage but because of the websites that have been targeted.
First up was Brian Krebs, a renowned internet security blogger who has made his career breaking stories on data breaches, online fraud and hackings. His website was among the first major victims of the massive Mirai botnet, powered by hundreds of thousands of IoT devices. In the face of what was then the biggest DDoS attack in history, weighing in at 600 Gbps, Krebs’ website went down for days, and his hosting company revoked their services as a result of the attack.
Soon after the Krebs attack, the Mirai botnet struck again in a major way, taking down DNS provider Dyn with a reported 1 Tbps attack. As a result of this attack, internet giants Netflix, PayPal, Twitter and Spotify, among many others, disappeared from the internet for hours despite presumably having top of the line security measures implemented.
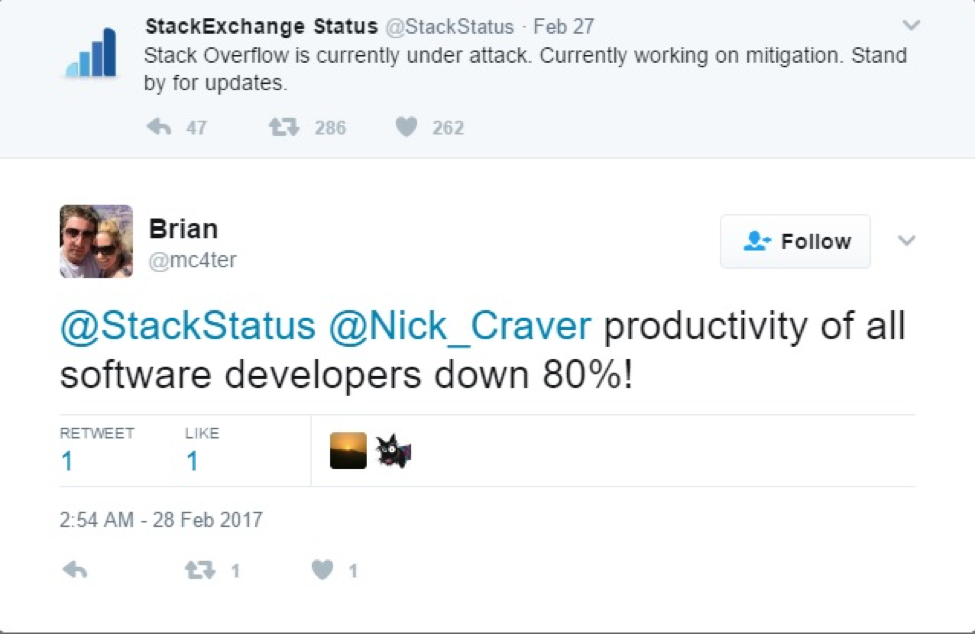
Another unlikely target buckled under a DDoS attack in February when Stack Overflow, the internet’s biggest question and answer site for programmers and a favorite of tech experts the world over, was taken down on a Monday.

Amusingly enough, a search on the Stack Overflow site for DDoS-related topics turns up a page in which a question asking for information on the best way to protect against DDoS attacks was closed for being off-topic.
The only specifics released in regards to the attack have come from Stack Overflow’s site reliability engineer Nick Craver, who reported that the site was receiving 40,000-50,000 requests per second for six plus hours. The requests apparently came from a botnet made up of compromised webcams, CCTV and DVRs – likely one of the absurdly sized IoT botnets currently dominating the DDoS landscape. Craver indicated that neither he nor the rest of the Stack Overflow team would be forthcoming with more information on the botnet behind the attack, stating that the secrecy was for the greater good as some of the efforts being made to stop such botnets cannot be publicly discussed for legal and privacy reasons.
Getting on-topic
It may have been off-topic for Stack Overflow, but it’s on-topic here: the best way to protect against distributed denial of service attacks is by investing in professional DDoS mitigation. Cloud-based protection provides scalable mitigation for websites and organizations of all sizes, protecting effectively against network layer, application layer and protocol attacks by inspecting traffic at a granular level in order to keep malicious traffic from reaching the protected website’s network while allowing legitimate traffic through to the website uninhibited, even during an attack.
As the high-profile attacks of the last six months have shown us, not only is there no shame in needing professional DDoS protection, there might just be some shame in not having adequate DDoS protection. Everyone is a target, no matter how unlikely it may seem.
Anna Jones is an experienced freelance writer specializing in the latest cyber security trends and news. She is keen to share her knowledge and expertise in the field and loves taking on a writing challenge!
[adrotate group=”7″]




 We are in our 11th year, and Global InfoSec Awards are incredibly well received – helping build buzz, customer awareness, sales and marketing growth opportunities, investment opportunities and so much more.
We are in our 11th year, and Global InfoSec Awards are incredibly well received – helping build buzz, customer awareness, sales and marketing growth opportunities, investment opportunities and so much more.