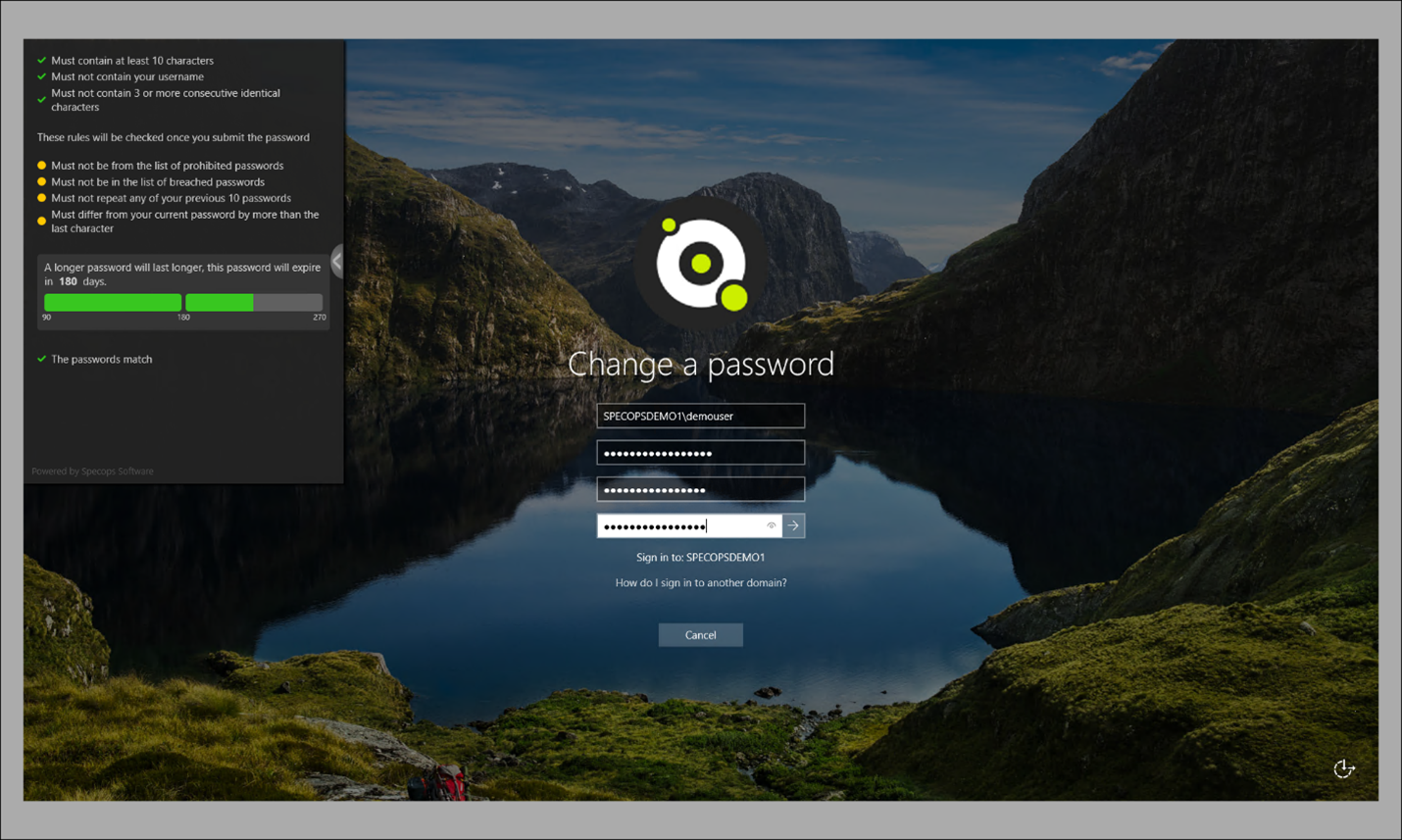
Looking for a tool to validate if your Active Directory (AD) passwords are safe across your Enterprise? Why would this be important? There are a few solutions in the industry that can provide a complexity enforcement and validate the password does not contain a dictionary word, which makes the solution have gaps. There hasn’t been a tool until now that will look for passwords that have been exposed or obtained through a breach. IT Security professionals are always looking for solutions that can make the organization more secure without breaking the bank.
Before we get to the details of the tool, let’s think about what we are attempting to solve by understanding the use of password, enhancement of technology and Multi Factor Authentication (MFA).
Authentication Background:
Passwords should always be a mix of alphanumeric (upper and lower characters) and a special character (i.e. %*%*). This is called a complex password. The length of the password makes a big difference. For example, 8 characters may take a few minutes while in some instance, the Microsoft recommended password length is 12 – 14 and can take a time greater than when password is normally changed. How do we enhance or better protect the access to the corporate information? Multi Faction Authentication (MFA) was created to add another complex solution for more security.
Multi Factor Authentication better known by the acronym as MFA. MFA is a second type of authentication that uses something you have besides the computer, a token that has changing numbers, or a phone with an application with changing numbers. MFA is not the fix all for access management. There are techniques that are used to bypass MFA. Use the key word search for “how to bypass MFA” and you will find close to and endless number of ways to move past MFA controls. We need to focus on the entire solution.
Understanding the Risk:
Now with a basic understanding of passwords and MFA, what’s the risk? The past year there has been a significant increase of cyber-attacks causing mayhem across a number of industries costing billions in fines, ransoms from Ransomware, and additional investment of people, process and technology to protect the company. A small investment in protecting the organization can save millions and potentially billions of dollars. One area which has been increasingly expensive is cyber insurance where if a company has been breached makes it increasing difficult or impossible to obtain a policy. Wouldn’t it make sense to make an investment where you have been controls in an effort to reduce the possibility of a breach?
The most common approach attackers use is phishing the users into thinking they have an immediate need to complete something. This leads them into gaining access to an enterprise IT infrastructure. It only takes one person out of many people to have an entire enterprise compromised. You are thinking they exploited a weakness; you are correct the user. How is this done?
Today’s attackers are much more intelligent and are very skilled in attacking organizations. They can be state sponsored, organized crime units and just very smart people looking to either do damage or financially motivated. It starts with who to they want to target. Research on the company to understand what do they have on the company that is available for free or pay for information. In some instances that are complete profiles of the organization, users, passwords, VPN or weakness in software. Through some research of forensic “how did this happen?” we learned that users use the same password across all of their personal access along with work.
So, the attacker finds a list of users that are using their company email for registration on a given website, the site gets compromised and the information is cataloged in a database free for the attackers. The attacker then attempts to use the access they found and determine if the access works. If it works, then they can test internally to see how far they can go in an environment.
The Solution to Reduce Risk:
Let’s move into the tool that provides a better way of protecting users in an enterprise and can benefit them in their personal lives.
One of the concerns is introducing new tools into a small or large enterprise is impacting the business and the staff learning how to use the tool. Specops Password Policy simplifies the process. The tool use some of the capability of AD and adds additional features of dictionary and Darkweb password detection.
Before we start with the installation of the tool lets take an assessment of the environment to see what gaps exist in AD for access management. The FREE tool is located https://specopssoft.com/product/specops-password-auditor/#tryfree. The result of a couple of companies that are over 10,000 employees indicated and average of 16% of the accounts had passwords that were discovered in a Darkweb database, collected from passwords found in leaks, as well as passwords being used to attack network honeypots right now. This result was one of the 8 criteria checked and provided actionable items to address. With the summary of the environment and ability to show exact weakness and management of the environment is a sure win to gain funding from the CIO, CEO or a Board of Directors.
The screenshot below is the presented view of a test environment.
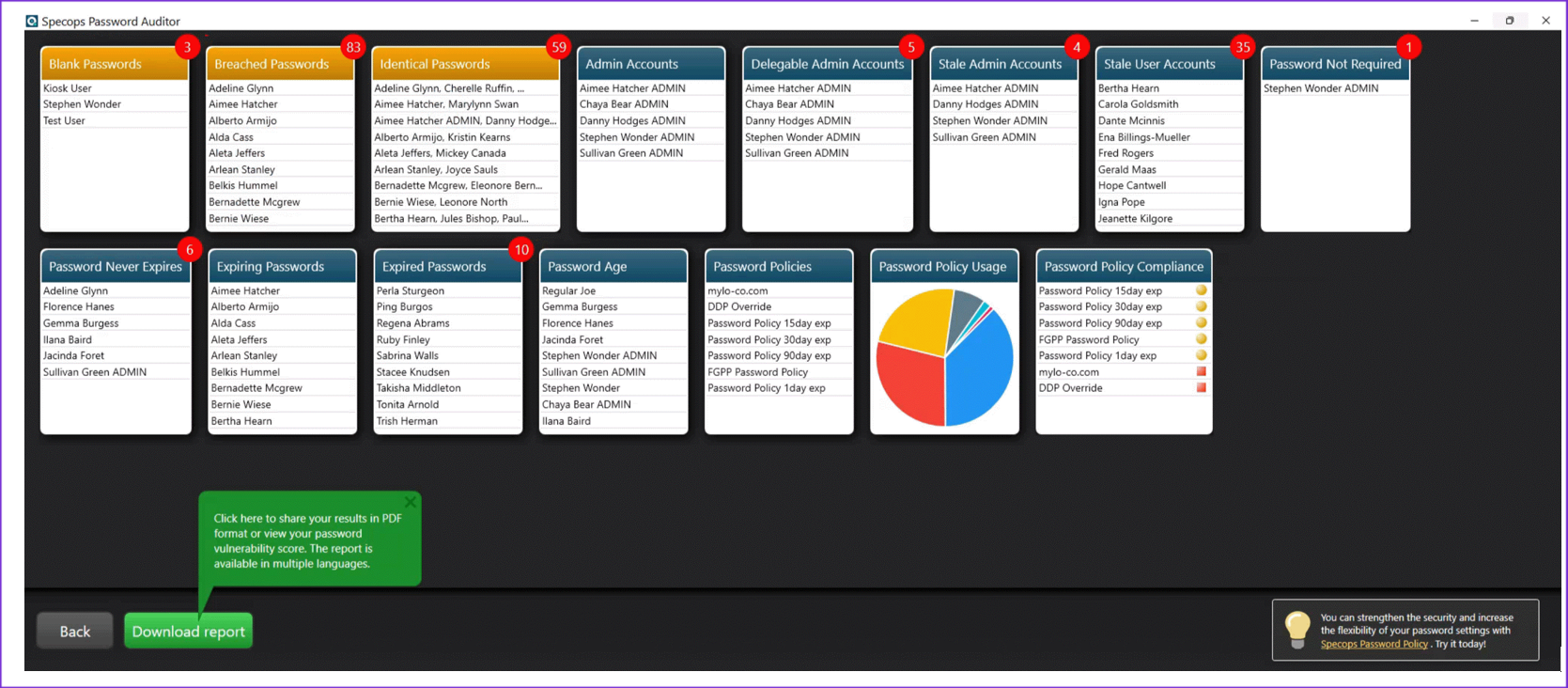
The executive view is easy to read and the reports detail the results provide the actions the IT team can work on remediating the environment.
Moving on to the application that makes the risk of access management a thing of the past, or at least less of a concern.
Specops Password Policy available https://specopssoft.com/product/specops-password-policy/ as I mentioned is a tool that easily integrates with an On-premise/Hybrid AD solution. The installation took an hour to install the application and configure to meet the needs of the organization we were testing. The long pole is the agent that is installed on the client workstations where depending on the deployment model can take several days. In the test environments it was less than a few minutes for a around 100 assets connected via a wired and wireless network.
The general screen familiar settings available in AD, with added a feature to guide a user to creating a strong password. The majority of the other tabs provide more granular controls than what AD provides, allowing the administrators to force uses in creating strong complex passwords.
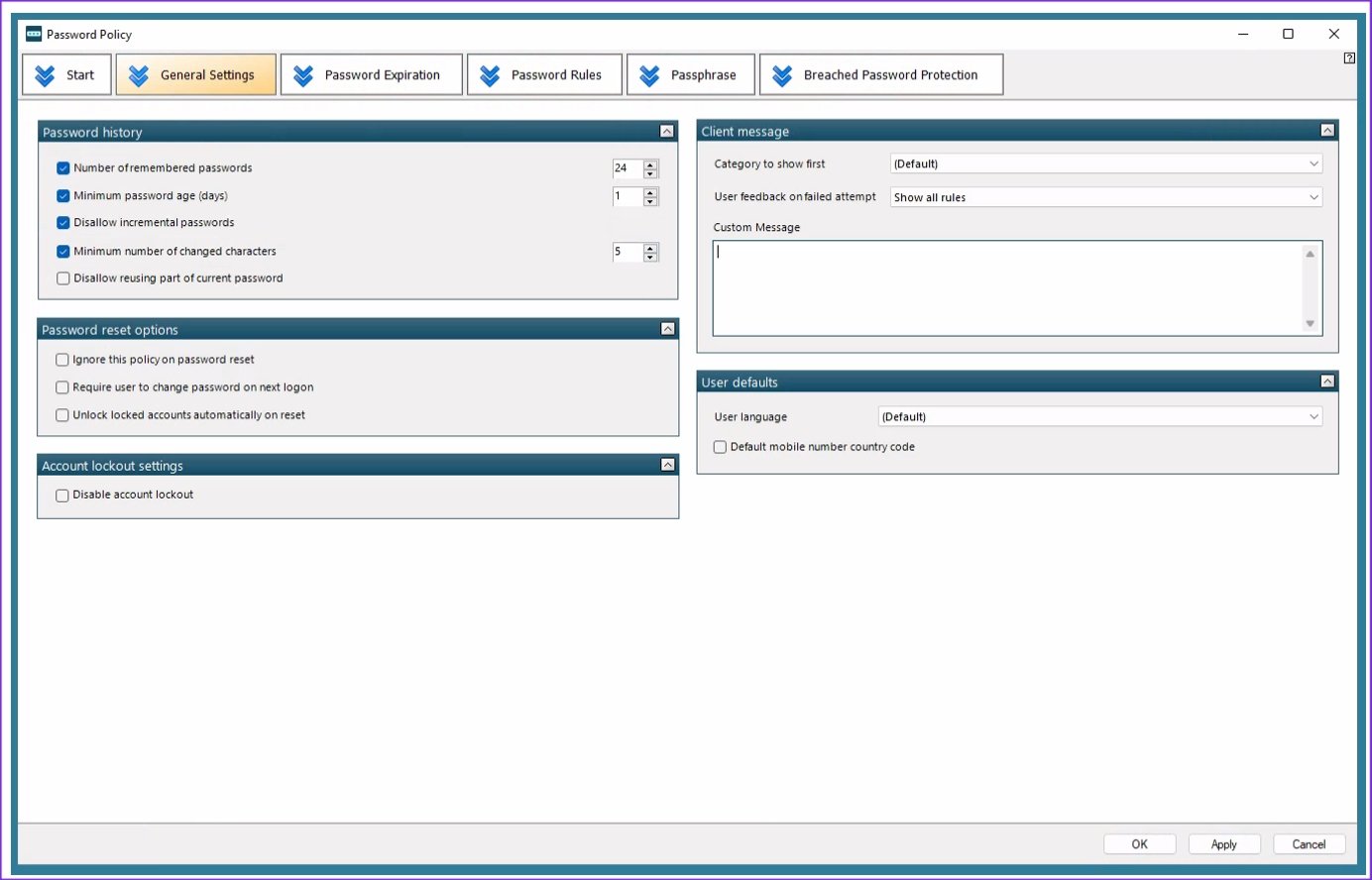
The feature which has this product above all of the products reviewed is below, allowing the Administrator to check any password that has shown up on the Darkweb along with passwords collected from breaches, as well as passwords being used to attack network honeypots right now.
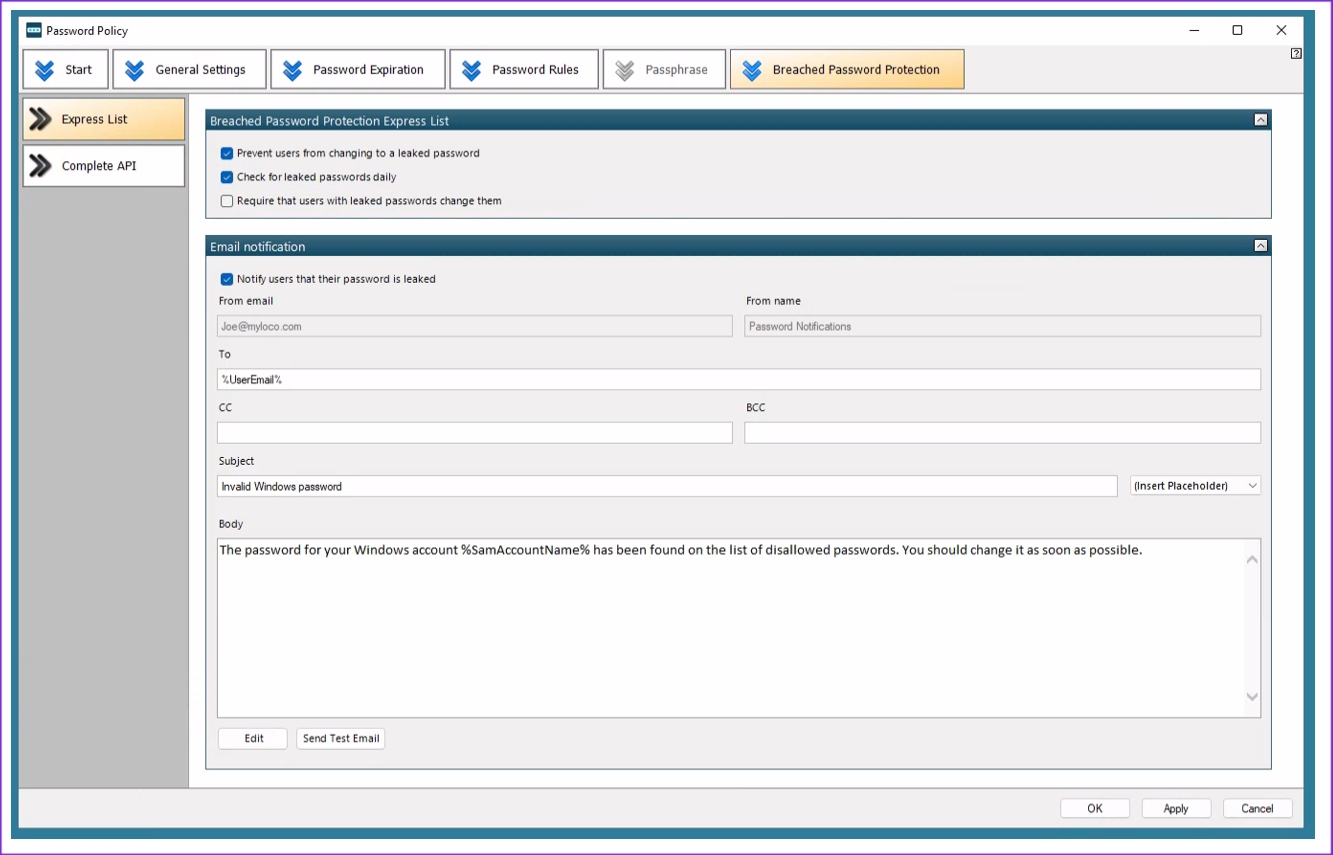
The database containing the password (hashes) is updated as information becomes available. The Darkweb is monitored daily.
In Summary, after 40 years in technology and watching technology grow from mainframes to personal PC’s, handle held phones, with a wide variety of operating systems this is one of the tools that at the start makes a difference in providing a safer environment for the rapid advancing threats from intelligent or state sponsored attacker.
The Security Professional goal is not to only secure an Enterprise but to teach people how to protect themselves from bad actors. Specops Password Policy moves the needle beyond any method to date.
Overall Review Score: 9.8 out of 10
Key Benefits:
- Interfaces are familiar to an Active Directory Administrator
- Solution integrates Cyber Intelligence into the solution to protect users from using know passwords which have been compromised
- Enforces complexity beyond Microsoft complex password requirements
- Free password assessment showing value of having Specops Password Policy
Key Features and Scores
- Seamless integration with AD and Hybrid solutions
- Easy for users to manage the interface
- Clear requirements listed on the screen for users
- Users are preventing from using simple password and are validated
Ease of Use: Score: 9.8
Does not require intimate knowledge to install and manage the application.
Platforms Supported: Score: 9.5 out of 10
Integrates with On Premise solely or in a Hybrid solution.
Customer Support and Documentation: Score: 9.9 out of 10
Specops provides extensive online support for Authentication and Password Management facilities, starting with Password Policy and all aspects of the recovery, notification, reset, and synchronization programs.
Pricing: Score: 10 out of 10
Specops Password Policy is priced based on the number of Active Directory users in scope. It follows a volume-pricing model where the price per license decreases as the number of users in scope increases. Specops Password Policy can be purchased as an annual subscription that includes technical support and product upgrades.
Source: Cyber Defense Test Labs Team



 We are in our 11th year, and Global InfoSec Awards are incredibly well received – helping build buzz, customer awareness, sales and marketing growth opportunities, investment opportunities and so much more.
We are in our 11th year, and Global InfoSec Awards are incredibly well received – helping build buzz, customer awareness, sales and marketing growth opportunities, investment opportunities and so much more.