- Contact
- Home
- Subscribe
- Magazines
- News
- Write for Us
- Research
- Artificial Intelligence (A.I.)
- Whitepapers
- Reviews
- Cyber Defense Test Labs: Review of Specops Password Policy
- Attivo Networks – One Year Later
- Future inTense Analysis: Guarding the Keys to the Kingdom – Attivo Networks ADAssessor
- Future inTense Analysis: Attivo Networks BOTsink
- Future inTense Analysis: Infocyte
- Future inTense Analysis – Stellar Cyber
- About Future inTense Reviews
- Platforms
- Contact
 LI
LI TW
TW FB
FB



 Charlie Thomas
Charlie Thomas

 Lena Allen
Lena Allen
 Vishakha Sadhwani
Vishakha Sadhwani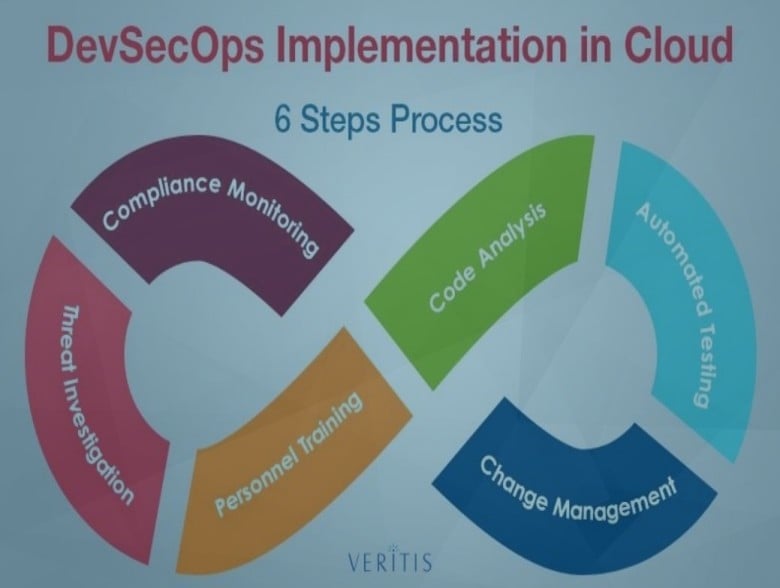
 Caroline McCaffery
Caroline McCaffery
 Brian Hesse
Brian Hesse
 Chris Scheels
Chris Scheels
 Jaye Tillson
Jaye Tillson
 Rishi Baviskar
Rishi Baviskar
 Wade Ellery
Wade Ellery
 Roy Kikuchi
Roy Kikuchi
 Sercan Okur
Sercan Okur
 Dan Anderson
Dan Anderson
 Erik Holmes
Erik Holmes
 Milica D. Djekic
Milica D. Djekic
 Boris Khazin
Boris Khazin